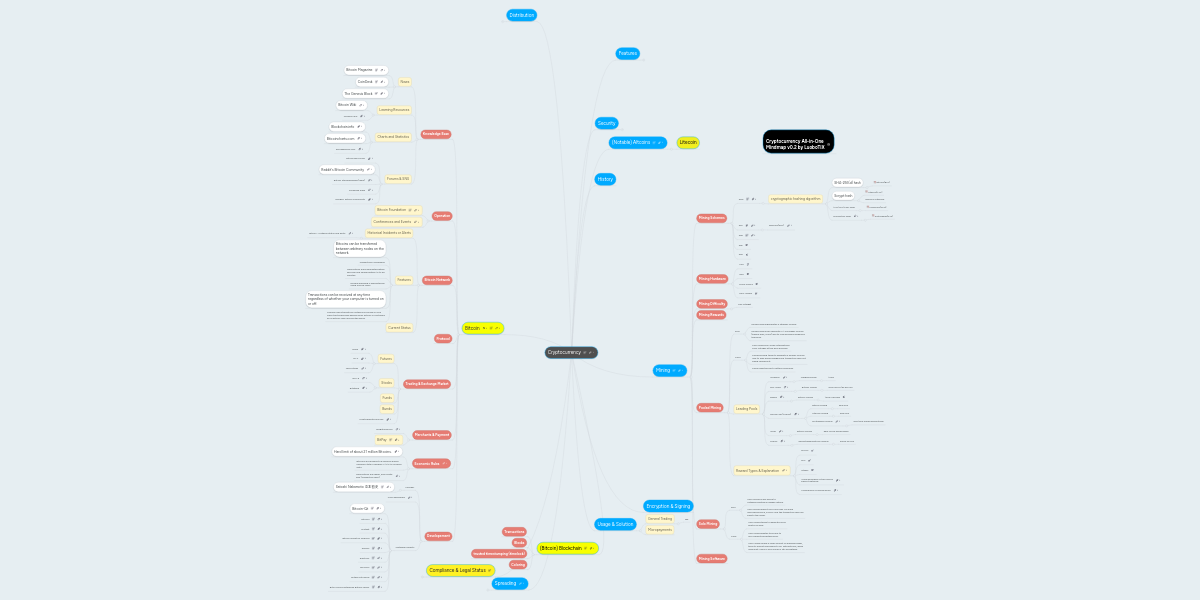
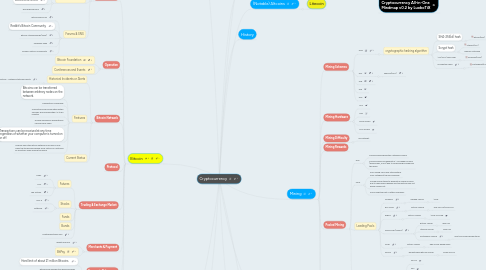
Cryptocurrency Algorightm Map
Many algorithm names can map to the same class. When cryptography is involved its a one-way function.

Cryptocurrency Hash And The Difference Between Sha 256 And Scrypt Cryptocurrency Algorithm Understanding
One crypto map can be applied to an interface.
Cryptocurrency algorightm map. Use the show crypto-local ipsec-map command to display the certificates associated with all configured site-to-site VPN maps. One of the first cryptocurrencies to use scrypt as a hashing algorithm. Creates or modifies a crypto map entry and enters the crypto map configuration mode.
The most popular hashing algorithm is SHA-256 which outputs at a length of 256 bits. A first step of many cryptography projects be it preparation for Cloud migration crypto agility or improving application security is to map out the cryptography actually in use in an applicationA naive approach would be to just review the source code and search for cryptographic calls. There must be no way to reverse the output value to calculate the input.
FPGA mining in the cryptocurrency world is a new emerging trend set to change the way blockchain-based coins and tokens are mined due to being very efficient in comparison to GPU and CPU mining performances. Every hash value is unique. Has an unusual encryption algorithm and is focused on decentralized trade.
These consensus algorithms have considerable effects on security inflation rates and the overall value of. Same crypto map can be applied to multiple interfaces. Now how does it work.
In less than a decade things drastically changed due to a variety of reasons. The idea is derived from the breakthroughs that Diffie-Hellman had. What is the RSA algorithm.
Proof-of-Stake PoS Delegated Proof-of-Stake DPoS are used in such blockchains as Tezos EOS and TRON respectively. The current CoinMarketCap ranking is 1 with a live market cap of 685197731073 USD. We can now configure the other aspects of the VPN such as the crypto map and ACL to match interesting traffic.
Bitcoin is down 570 in the last 24 hours. Augur uses power to predict financial markets Dash. The RSA algorithm is the most widely used and popular asymmetric cryptographic algorithm in history.
Supply of 21000000 BTC coins. Virtually eliminate tracking of the sender. The name attribute can be either a string that is used when calling the SystemSecurityCryptographyCryptoConfigCreateFromName method or the name of an abstract cryptography class in the SystemSecurityCryptography namespace.
Todays crypto mining ecosystem is not as we knew it years ago. Output length of hashing algorithm must be fixed a good value is 256 bytes Even the smallest change in input data must produce significant difference in output. FPGA or a Field Programmable Gate Array is a unique integrated type of a blank digital circuit used in various types of technology and.
This is usually based on the notion that markets have momentum and you want to be on top of that momentum. It is named after MIT professors Rivest Shamir and Adleman who discovered this algorithm. Syscoin is not a cryptocurrency plus a platform - it is a platform built into a cryptocurrency.
Sep 15 2017 1 min read. A few facts about crypto map. To accommodate multiple tunnels crypto map.
The live Bitcoin price today is 3659030 USD with a 24-hour trading volume of 38177595995 USD. Whatever rules that you use in order to inform your daily trades you can code into a cryptocurrency algorithm. Crypto map interface IPsec Applies a previously defined crypto map set to an interface.
Use the tag option to display certificates associated with a specific site-to-site VPN map. The element maps a class to one friendly algorithm name. Mapping the Crypto in Applications.
Specifies and names an identifying interface to be used by the crypto map for IPsec traffic. There are a few requirements that a good hashing algorithm needs. It has a circulating supply of 18726212 BTC coins and a max.
Same input will always produce same output. ArubaOS supports site-to-site VPNs with two statically addressed controllers or with one static and one dynamically. One of the most well known technical indicators are those of trends.
The first and most widely used decentralized ledger currency with the highest market capitalization. Hashing is the act of mapping data of any length to a fixed-length output. While a projects roadmap and business efforts are essential the different blockchain protocols and consensus algorithms used can play a prominent role in the success of a cryptocurrency.
There are numerous technical indicators that try to map trends. Because of the arrival of complicated ASIC miners Application Specific Integrated Circuit and the increase of the difficulty in the network of most cryptocurrencies the majority of the coins are currently impossible to mine with just the use of a. If you just need a hash for a unique ID and not cryptography which one is the fastest.
Proof-of-Authority PoA is a modified algorithm of PoS that suits private networks and big corporations like for example Microsoft Azure. Crypto map R1-R2-CRYPTO-MAP 10 ipsec-isakmp set peer 10002 set ikev2-profile R1-R2-PROFILE match address R1-R2-ACL. Nodejs supports hashing data using three algorithms and two digests.
Even the tiniest alteration to the data being hashed caused the entire value to change. Ip access-list extended R1-R2-ACL permit ip 192168100 000255 192168200 000255. Crypto map is a feature binding all the information we discussed before in this section and previous together.
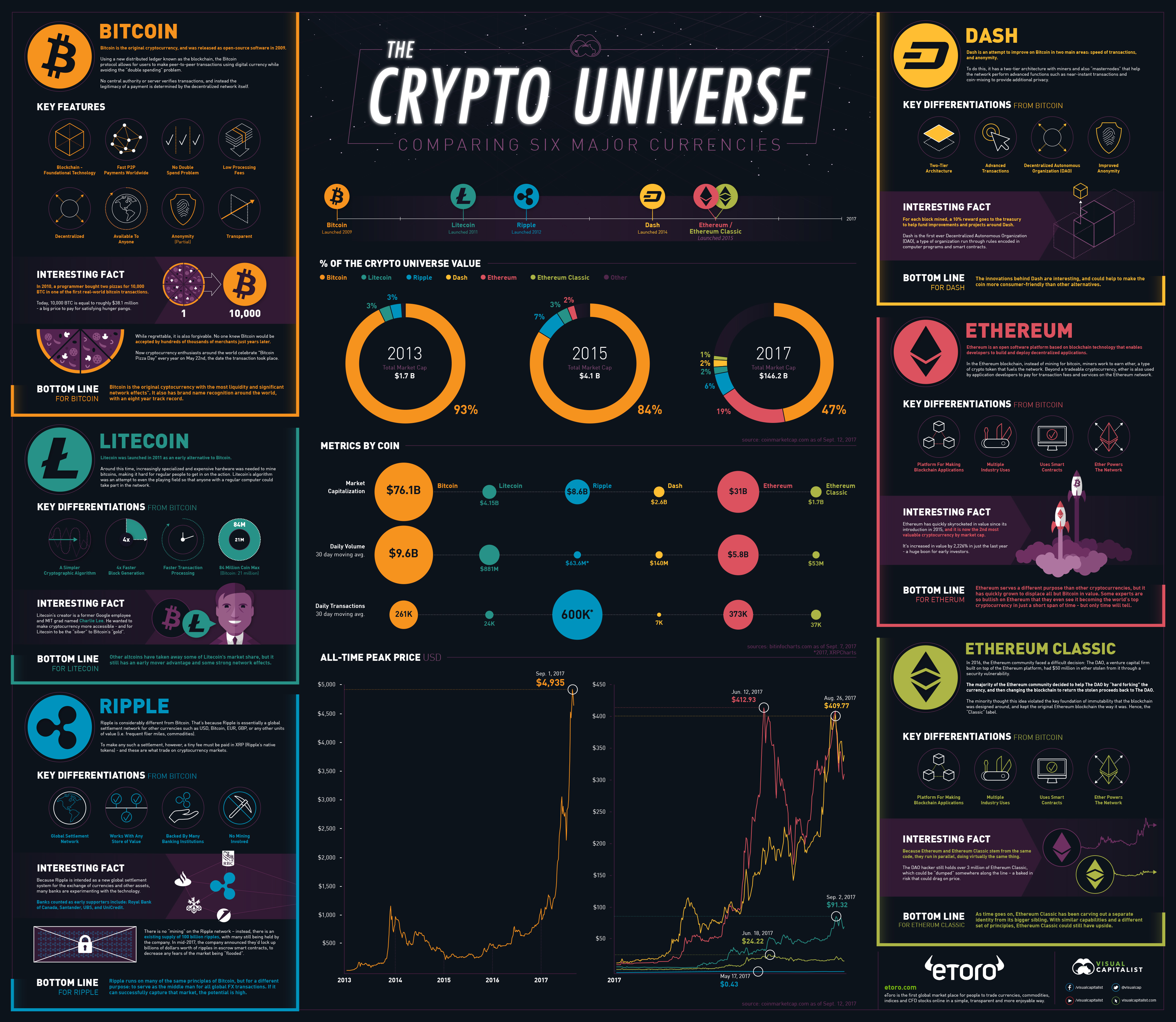
This Giant Infographic Compares Bitcoin Ethereum And Other Major Cryptocurrencies

Mindmap Abstraction Of The Different Types Of Blockchain Applications Download Scientific Diagram

Not All Blockchains Are Born Equal Finding The Right Consensus Algorithm Coinspeaker Blockchain Technology Blockchain Algorithm

A Blockchain Terminology Concept Map By Michele Mostarda Lotus Fruit Medium
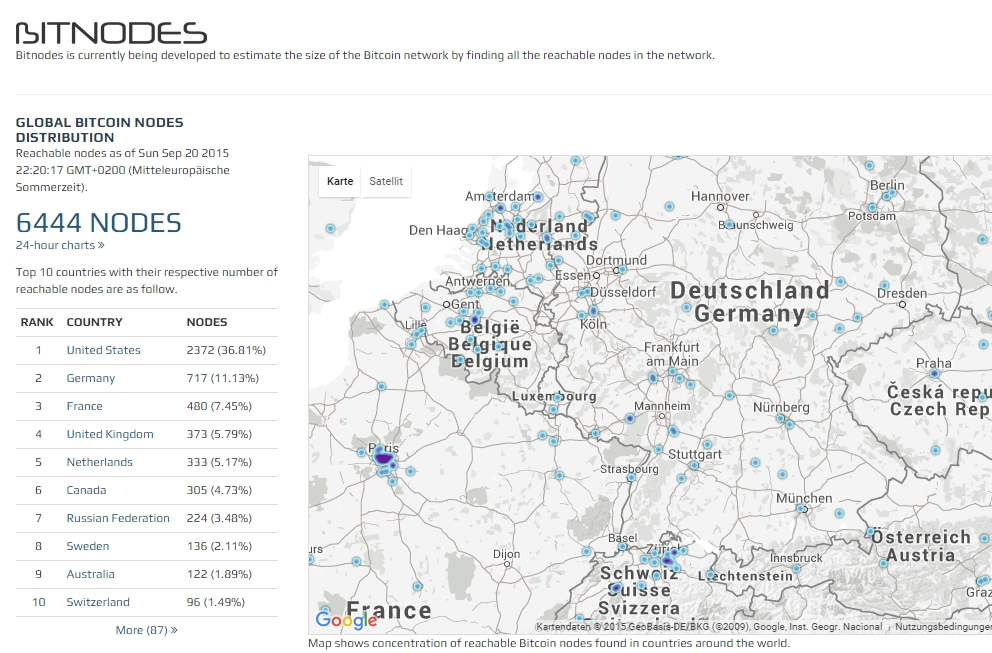
Visualizing The Blockchain The 7 Most Beautiful Bitcoin Visualizations Datalion
Btc Bitcoin Algorithm Decoded 80 Win Rate In Bear Market Strategy By Ryuzakitrader Tradingview

Comparing Bitcoin Market Cap Black Line With Predicted Market Cap Download Scientific Diagram
Cryptocurrency Mindmeister Mind Map

Mining Algorithms Of Bitcoin Ethereum And Other Popular Cryptocurrencies Each Cryptocurrency Uses A Certain Encryption Algorithms Cryptocurrency Bitcoin Cash
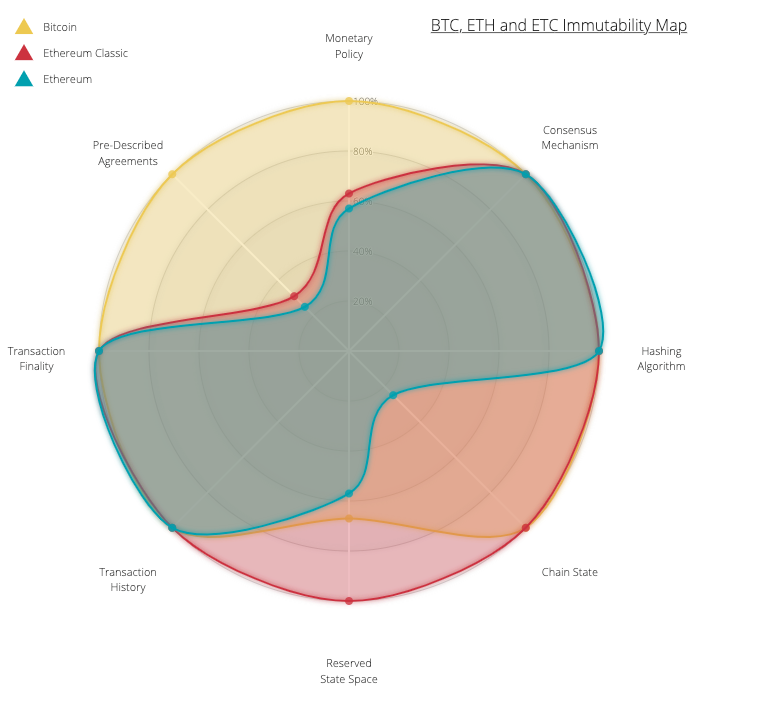
Quantifying Immutability Understanding How Immutability Changes By Yaz Khoury Medium

Correlation Of Major Cryptocurrencies Exemplified Through A Heatmap Download Scientific Diagram

Pin By Dan Williams On Cryptocurrency Risk Management Cryptocurrency Pie Chart

Bitcoin Difficulty All About Cryptocurrency Bitcoinwiki

Cryptocurrency Market State Crypto Mining Blog

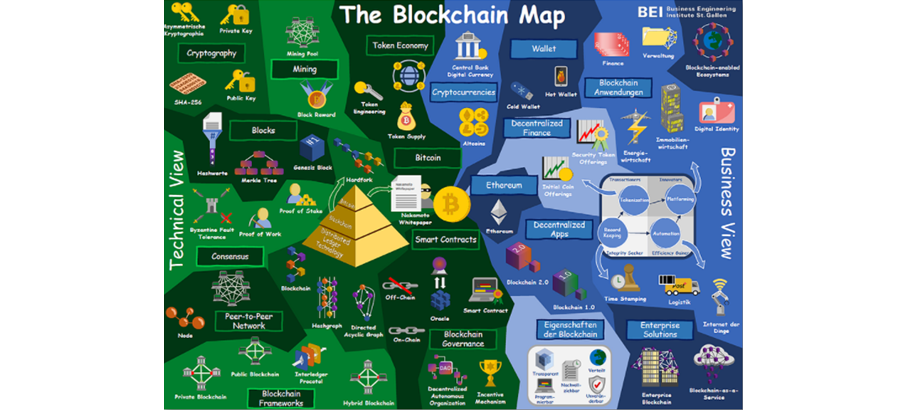
The Technical Side Of The Blockchain Map Ccecosystems News
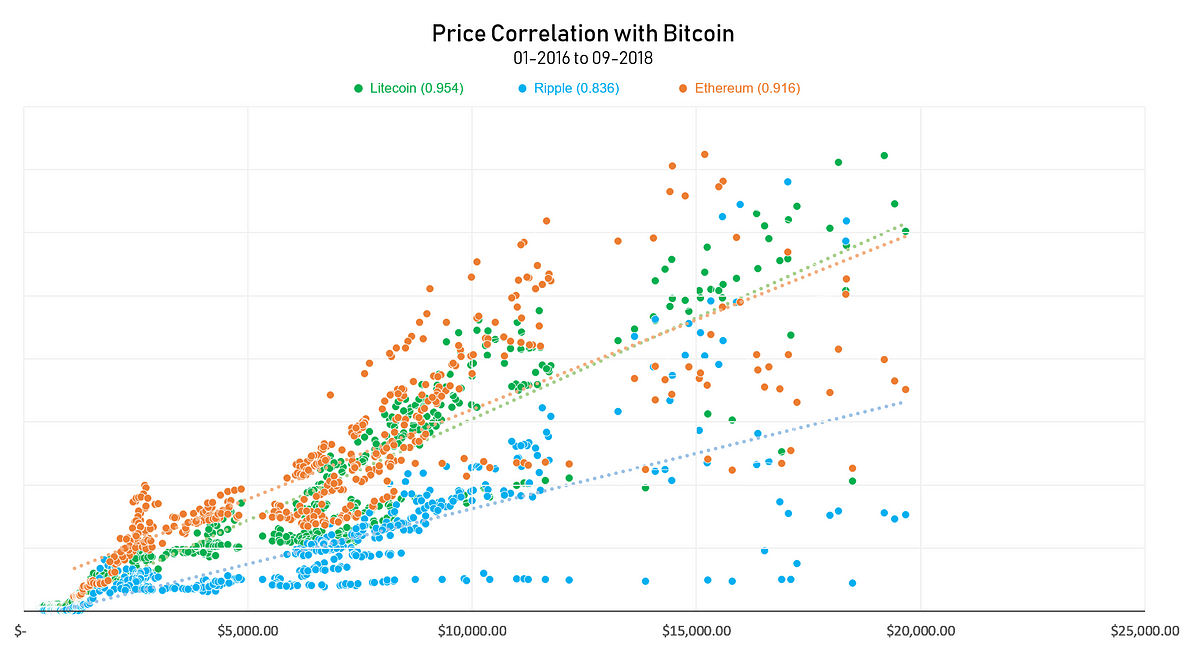
You Don T Need A Diversified Crypto Portfolio To Spread Risk Here S Why By Kenny L Towards Data Science
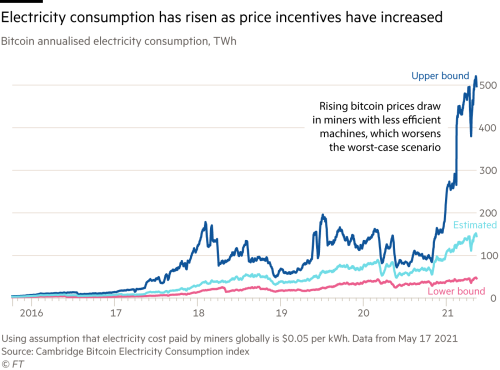
Bitcoin S Growing Energy Problem It S A Dirty Currency Financial Times